In a previous blog article, we discussed the main steps in a phased migration of a distributed control system (DCS), which are:
- Phase 1 – Operational infrastructure and human-machine interfaces (HMIs)
- Phase 2 – Migration of industrial controllers, I/O and control programs
In this article, we discuss the first aspect of Phase 1 in greater detail, i.e., upgrading the operational infrastructure.
To start, a modern DCS relies on an array of systems that can look like IT systems but are tailored specifically to be used in OT infrastructure. The following systems must be in place for the solution to be viable:
- Physical: fibre optics, copper, wireless, etc.
- Routing and switching: switches, routers and firewall
- Servers: applications, databases, etc.
An architecture that meets specific project needs is fundamental. It must clearly define the roles of the users, machines and servers needed for solution implementation, while meeting the highest standards in cybersecurity, redundancy and resiliency. The architecture must permit clear segregation of information technologies (IT) and operations technologies (OT) and establish methods for making the required exchange of information between the two systems available.
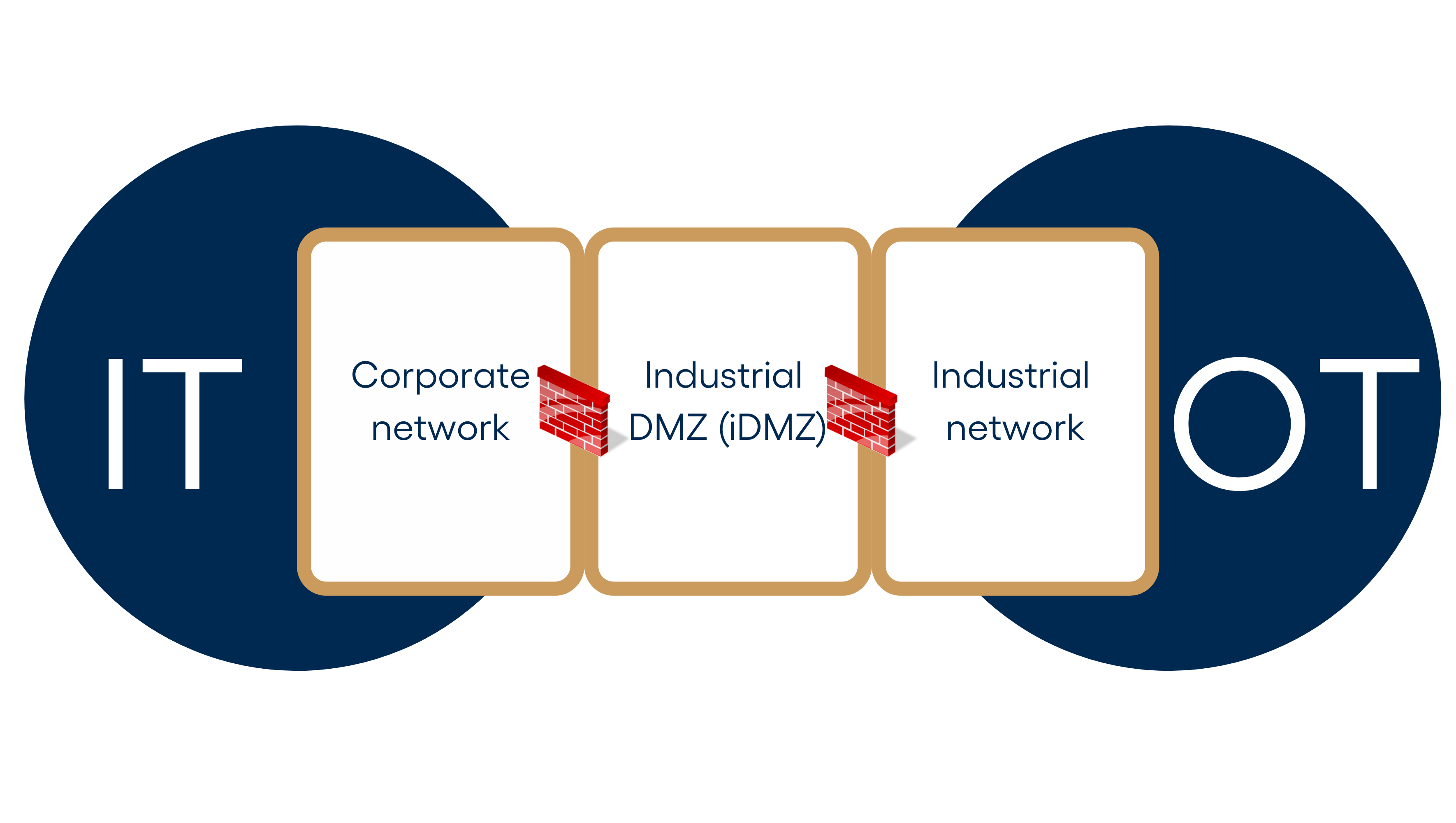
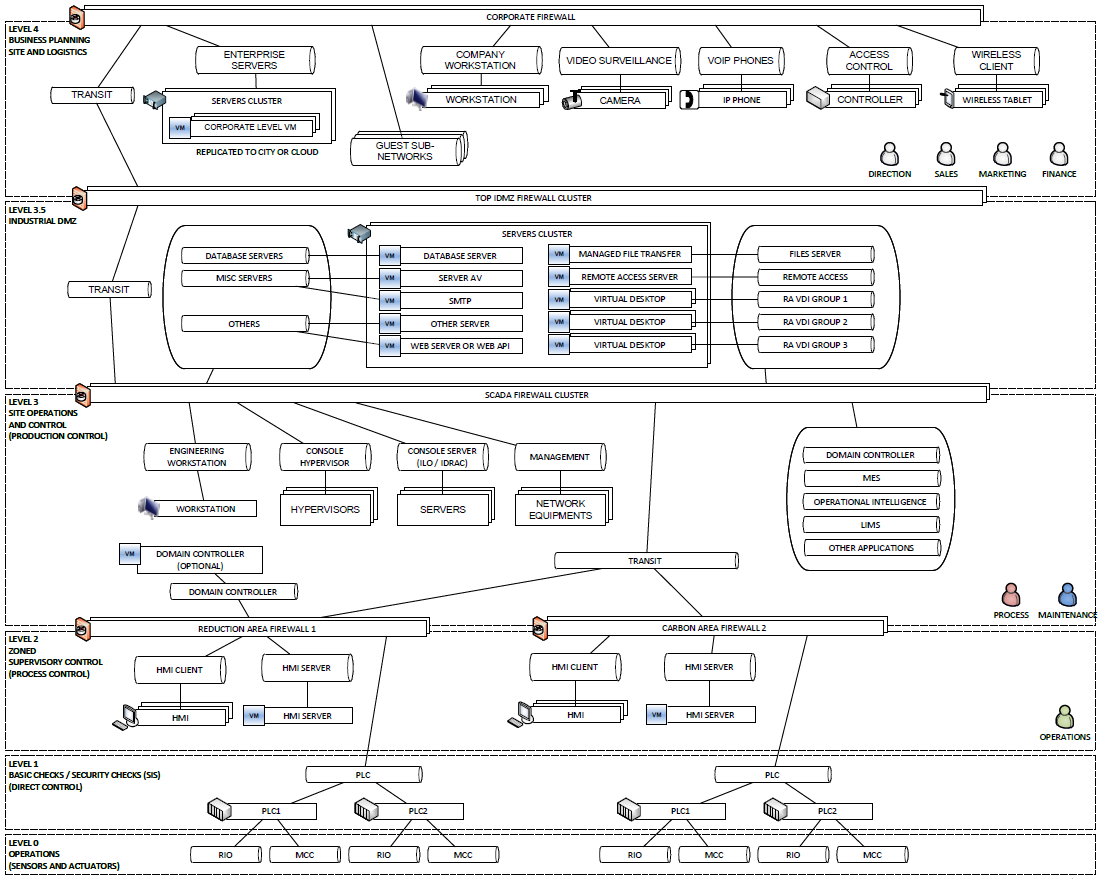
As we described earlier, just adding switches or other network devices to connect various pieces of equipment to your industrial network is not enough to mitigate the possible cybersecurity risks. You need to have a work plan that is defined by the system architecture. Regardless of the size of your operational infrastructure, it is a good idea to segregate it into different sectors to clarify the purpose and area of responsibility of every piece of equipment in use:
Corporate network (IT)
- Already exists, under IT team responsibility
- Contains all systems that meet the company’s needs
- Notably includes the corporate data historian
Industrial DMZ (iDMZ – IT/OT)
- Generally needs to be defined
- Contains all systems of exchange required for adequate operation of the underlying industrial network
- Dedicated Windows Server Update Services (WSUS)
- Antivirus signature services
- Secure file transfer
- Industrial network back-up system
- Intermediate data historians
- Industrial network asset tracking system: SolarWinds, WhatsUp Gold, etc.
Industrial network (OT)
- Generally needs to be defined
- Contains all industrial systems necessary for production
- Operations consoles
- Industrial controllers
- Main industrial network backup system